How Secure is the Bitcoin Network?
The heart of Bitcoin’s network security lies in the SHA-256 hashing algorithm. SHA-256 is a cryptographic hashing function that protects transaction records and makes them tamper-proof (immutable).
Bitcoin uses SHA-256 to secure every block in the blockchain and power its mining process. This same algorithm also serves as the security backbone for services you use daily—from Amazon Web Services securing your online shopping, to Google Chrome protecting your web browsing, to the Apple App Store verifying every app download.
Key Takeaways
-
SHA-256 (Secure Hash Algorithm 256-bit) is the cryptographic foundation that secures the Bitcoin network, making transactions tamper-proof.
-
SHA-256 secures not just the Bitcoin network but also everyday IT services such as Amazon Web Services and app store downloads.
-
Breaking SHA-256 through brute force would theoretically take longer than the age of the universe, even if every computer on earth combined their efforts.
-
Quantum computers could theoretically reduce cracking time, but would ultimately still be unable to feasibly crack SHA-256.

What Is Cryptographic Hashing
At its core, cryptographic hash functions are mathematical algorithms that transform any input (text, numbers, or data) into a fixed-length string of characters. SHA-256 specifically transforms any input—whether it’s a single letter, an entire book, or a massive database—into exactly 64 characters (representing 256 bits of data). The security feature of hashing functions is that it is easy to compute one way (hashing your data), but mathematically infeasible to compute in the reverse order (deriving your data from the hashed 64 characters).
Here’s a simple math analogy: Let’s say you start with the number 7. Now perform these operations in order: multiply by 13, add 29, multiply by 8, subtract 15, then multiply by 47. You get 12,561 as your final answer. Going forward (Computing 7 into 12,561) is easy if you know the steps. But if someone only gave you the final number 12,561 and asked you to find the original number, you’d have to try millions of different combinations to work backwards—and that’s with just 5 simple steps! SHA-256 uses 64 rounds of incredibly complex mathematical operations involving bitwise rotations, additions, and logical functions. Even with the world’s most powerful computers working together, reversing SHA-256 would take longer than the age of the universe.
Key Properties of Secure Hash Algorithm 256 (SHA-256)
Deterministic: The algorithm always gives you the same output for the same input. Type “Hello World” and you’ll always get the same hash.
Fixed Output Length: Regardless of whether you input a single letter or an entire encyclopedia, the output is always exactly 256 bits (64 characters when displayed).
One-Way Function: You can easily go from input to hash, but it’s virtually impossible to go backwards from hash to input. It’s like trying to unscramble an egg.
Avalanche Effect: Change even one tiny bit of the input (like adding a single comma), and the entire output changes dramatically. If you modify the data with small things, like a single space or a comma, it will completely change the hash output.
Collision Resistance: It’s virtually impossible for two different pieces of input data to generate the same hash, ensuring integrity and security in critical applications.
Try it out yourself! Key in anything you want and hash it at https://tools.keycdn.com/sha256-online-generator.
The History of SHA-256
SHA-256, a cornerstone of modern cryptography, emerged from the U.S. National Security Agency’s (NSA) efforts to strengthen cryptographic hash functions in the early 2000s. Published in 2001 as part of the SHA-2 family, it was designed to address growing concerns about the security of its predecessor, SHA-1.
Its adoption accelerated dramatically with the rise of Bitcoin in 2009, where SHA-256 became integral to the proof-of-work consensus mechanism. Today, it remains one of the most widely deployed cryptographic hash functions, securing everything from digital certificates and password storage to blockchain networks and secure communications protocols.
How SHA-256 Works (The Simple Version)
Think of SHA-256 as an incredibly sophisticated blender:
-
Input Processing: It takes your data and chops it into standardized chunks of 512 bits each
-
Mathematical Mixing: It performs 64 rounds of complex mathematical operations on each chunk
-
Final Output: After all the mixing, it produces exactly 256 bits of completely scrambled data
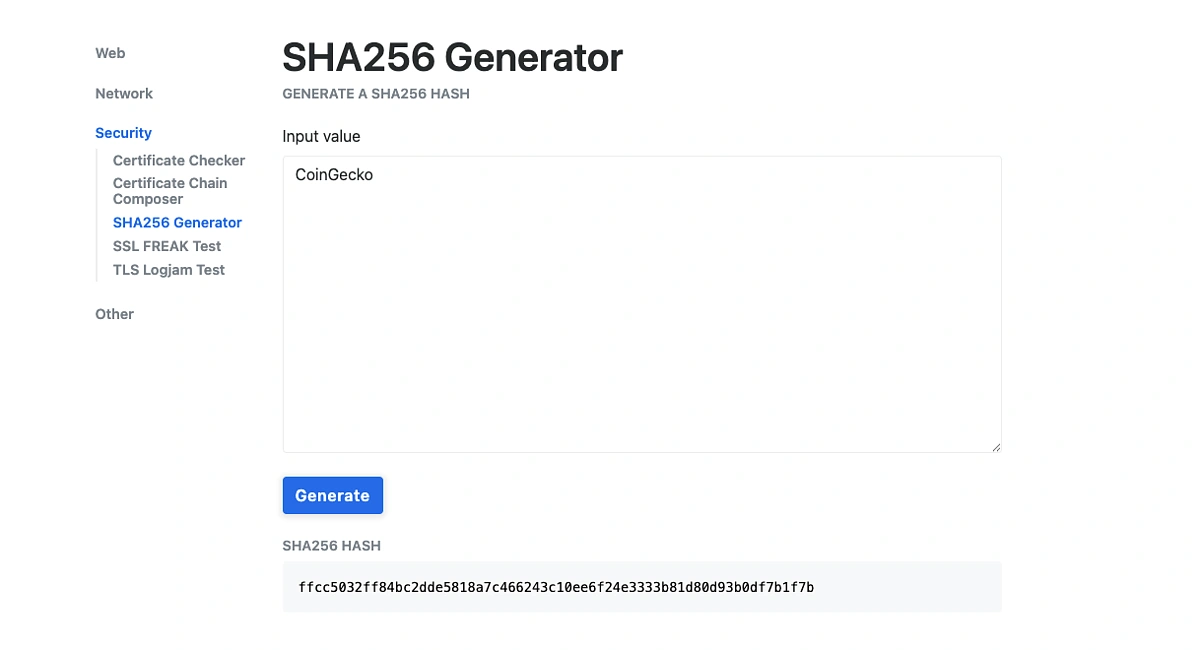
Real-World Example
Let’s see SHA-256 in action:
-
Input: “CoinGecko”
SHA-256 Output: ffcc5032ff84bc2dde5818a7c466243c10ee6f24e3333b81d80d93b0df7b1f7b
-
Input: “CoinGecko!!” (just added an exclamation mark)
SHA-256 Output: 8548ee03082e4945185015704b6bc6f0dc073030683ba924378aa07ead058dda
Notice how adding just one character completely changed the output! This is an important feature as it makes evidence of data tampering more apparent. An attacker cannot simply hide their tracks now by just changing a small bit of the data as it results in a completely different output.
How SHA-256 Is Used in the Bitcoin Network
Bitcoin doesn’t just use SHA-256 once—it actually uses double SHA-256 for extra security. If you’re hashing something in Bitcoin, you’re almost always using HASH256. This works by putting the data through SHA-256, then taking the result and putting it through SHA-256 again. Documentations however, show that double SHA-256 is not necessary but was implemented by the creator of Bitcoin, Satoshi Nakamoto, presumably as a safety precaution.
Two Critical Uses in Bitcoin
-
Mining and Proof of Work
Miners compete to find a nonce (a special number) that, when combined with a block of Bitcoin’s data (the data input) and hashed using SHA-256, produces a hash (output) that meets Bitcoin’s difficulty requirement. Think of it like a digital lottery—miners have a block of Bitcoin transaction data, and they add a special number (the nonce) to it, they keep trying different nonces, until they find a “winning” hash (the output) that starts with many zeroes. The number of zeroes required depends on the Bitcoin mining difficulty level, which adjusts every 2 weeks to keep block creation steady at roughly 1 block every 10 minutes.
SHA-256 proves that a miner who has successfully found the winning nonce did so through pure hard work (proof of work!), as finding a resulting hash that meets the requirements in any other way is unlikely.
-
Immutability
Each Bitcoin block contains the SHA-256 hash of the previous block, creating a link between blocks, a blockchain, if you will. If someone tries to alter a past transaction, it would change that block’s hash, but also cause each successive block to have mismatching hashes. This mismatch of block hashes invalidates the whole chain of blockchain data, which amplifies the evidence of data tampering in that set of blockchain data.
What It Takes to Crack SHA-256
Ever wondered why Bitcoin’s popular tagline is “vires in numeris?” That’s Latin for “strength in numbers,” because as you’re about to see, the numbers required to crack Bitcoin’s cryptographic foundation are truly astronomical. Let’s explore a hypothetical situation of what it would take to crack SHA-256.
The Brute Force Approach
To crack SHA-256 through brute force (trying every possible combination), an attacker would need to try up to 2^256 different possibilities. To put this number in perspective:
-
2^256 = 115,792,089,237,316,195,423,570,985,008,687,907,853,269,984,665,640,564,039,457,584,007,913,129,639,936.
-
This number has 78 digits.
Now, assume you have a giga galactic super computer (watch this fun video to learn all about that hypothetical!), that has the computational power of a thousand Googles. If everyone on earth had this computer and combined their efforts at breaking SHA-256, it would still take over 507 billion years to have a chance at finding the correct guess.
The Current Bitcoin Network’s Power
To understand the scale, consider that the current Bitcoin hashrate as of writing is 977.29 EH/s, representing the global Bitcoin network hashrate. This means the network performs nearly a quintillion (1,000,000,000,000,000,000) hash calculations every second.
If we could somehow redirect this entire network to crack a single SHA-256 hash instead of mining, it would still take far longer than the age of the universe to succeed through brute force.
The Quantum Computing Wild Card
Quantum computers represent the most realistic threat to SHA-256, but even here, the numbers are reassuring for Bitcoin holders.
Grover’s Algorithm Effect: A quantum computer using Grover’s algorithm could potentially reduce the complexity of cracking SHA-256 from 2^256 (theoretically secure against brute force attacks on classical computers) to 2^128 operations, which is still formidable but significantly less secure.
Current Reality: Even using Grover’s algorithm, it is currently believed to be essentially impossible to break a hash function like SHA256 according to a study by the National Academies Press.
Even if you disregard current assurances against the threat of quantum computing, the Bitcoin community has been aware of potential quantum threats since at least 2010, with ongoing research into post-quantum cryptography and migration strategies that could be implemented via a soft fork when needed.
Energy Requirements: The Ultimate Barrier
Even if someone built a super computer capable of trying every combination, the energy requirements would be astronomical. Breaking SHA-256 through brute force would require more energy than is available on Earth, making it not just computationally impossible, but physically impossible as well.
Beyond Bitcoin: Other Uses of SHA-256
SHA-256’s security has made it ubiquitous in the digital world:
Web Security: SHA-256 is used for authenticating Debian software packages and in the DKIM message signing standard; SHA-512 (also part of the SHA-2 standard) is part of a system to authenticate archival video from the International Criminal Tribunal of the Rwandan genocide.
Government Applications: SHA-1 and SHA-2 are the Secure Hash Algorithms required by law for use in certain U.S. Government applications, including use within other cryptographic algorithms and protocols, for the protection of sensitive unclassified information.
Digital Certificates: SHA-256 helps secure digital certificates used in HTTPS websites and secure communication protocols like TLS/SSL and SSH, where it verifies data integrity and authenticates certificates. It’s also widely used throughout Unix/Linux systems for verifying file integrity, software packages, and system security.
Conclusion: The Digital Fort Knox
Bitcoin’s security through SHA-256 represents one of the most robust cryptographic implementations in human history. The combination of mathematical impossibility (brute force cracking) and physical impossibility (energy requirements) creates a fortress that has withstood over 15 years of attacks from hackers, and critics.
The beauty of SHA-256 lies not just in its mathematical elegance, but in its practical application within Bitcoin’s ecosystem. Every transaction, every block, and every security guarantee depends on this 20-year-old algorithm that continues to prove its worth day after day.
While quantum computing represents a theoretical future challenge, the timeline for practical quantum attacks on SHA-256 extends decades into the future, giving the cryptographic community ample time to prepare post-quantum alternatives if needed.
For now, Bitcoin users can rest assured that their digital assets are protected by some of the strongest cryptographic techniques known to humanity, a mathematical function that would take longer to crack than the universe has existed.
This article is for educational purposes only and should not be considered financial advice. Cryptocurrency investments carry inherent risks, and past performance does not guarantee future results. Always conduct your own research and consider consulting with a qualified financial advisor before making any investment decisions.
Frequently Asked Questions
-
Can SHA-256 be broken?
No, SHA-256 cannot be broken with current technologies. Breaking it through brute force would require trying 2^256 combinations, a number so large that even if every computer on Earth worked together, it would take over 507 billion years to crack.
-
What happens if SHA-256 is compromised?
If SHA-256 were ever compromised, Bitcoin could implement a new cryptographic algorithm through a soft fork. The Bitcoin community has been preparing for this possibility since 2010, with ongoing research into post-quantum cryptography.
-
Why does Bitcoin use SHA-256 twice?
Bitcoin uses double SHA-256 (running the algorithm twice) as an extra security precaution implemented by Satoshi Nakamoto. While cryptographers agree this isn’t strictly necessary as single SHA-256 is already secure, the double hashing provides additional protection against certain theoretical attacks and was likely added as a conservative safety measure.
-
Is SHA-256 better than SHA-512?
SHA-256 isn’t necessarily “better” than SHA-512, they serve different purposes. Bitcoin chose SHA-256 because it provides sufficient security (256 bits) while being more efficient in terms of computational resources and storage space. SHA-512’s longer output (512 bits) would double the storage requirements without meaningfully improving Bitcoin’s security.
-
How long does it take to calculate SHA-256?
Calculating a single SHA-256 hash takes mere microseconds on modern hardware. A typical computer can perform millions of SHA-256 calculations per second. This speed is what makes SHA-256 practical for Bitcoin mining, where miners perform quintillions of hashes per second globally yet the one-way nature means reversing even one hash would take longer than the age of the universe.
-
Do all cryptocurrencies use SHA-256?
No, different cryptocurrencies use different hashing algorithms. While Bitcoin uses SHA-256, Ethereum uses Keccak-256 (a variant of SHA-3), Litecoin uses Scrypt, and Monero uses RandomX. Each algorithm has different properties regarding mining hardware requirements, energy efficiency, and resistance to specialized mining equipment (ASICs).
-
Can I mine Bitcoin without SHA-256?
No, mining Bitcoin specifically requires SHA-256 calculations. The entire Bitcoin protocol is built around this algorithm, from mining new blocks to linking blocks in the blockchain. Using a different algorithm would create an entirely different cryptocurrency that wouldn’t be compatible with the Bitcoin network. SHA-256 is fundamental to Bitcoin’s proof-of-work consensus mechanism.
